**This post is still a work in progress, only command execution as a limited user has been accomplished**
At the moment this is isn't all that impressive, sorry to anyone looking for 1337 sploitz.
Requires auth, runs as a limited user (apache).
One of the reasons that this device peaked my interest is the way that it's designed to run, it's intended to sit with one interface on the DMZ and another interface on the internal network. That's a gold mine as it lives in both worlds. The downside is that you have to start on the inside to get to the config interface, that you have to have the credentials to be able to log into, to start this. So this would be a post initial infiltration, and setting up persistent access type of thing. Plus no one is going to audit this machine as you don't get the root credentials when you buy it so it's about the most perfect device to setup as a persistent access point.
I recently had the opportunity to experiment with Shoretel's Mobility Router. While I was watching the demonstrator demo the unit I saw this page:
When I saw that it had the option to run some commands from the web interface I was very hopeful that this could be a command chaining vulnerability.
If I can define part of the command perhaps I can tag some extra stuff on the end and execute my own commands. Maybe I can add "; whoami" or "&& whoami" to the end and have the system execute this command instead of just ping:
ping $host ; whoami
This would ping the host, then as long as it was successful it would also execute whoami.
or
ping $host && whoami
This would ping the host and do a whoami.
Initially this didn't work, as the site filters all the characters that aren't alpha numerical. That includes the space character. So I couldn't type in " ; whoami" or "&& whoami". I also couldn't use %XX because the % character is not allowed. So I couldn't type what I wanted in to the field, I could only put in alpha or numerical input, no spaces, no special characters.
My next step was to see if the filters were on the webpage and the back end or just the web page.
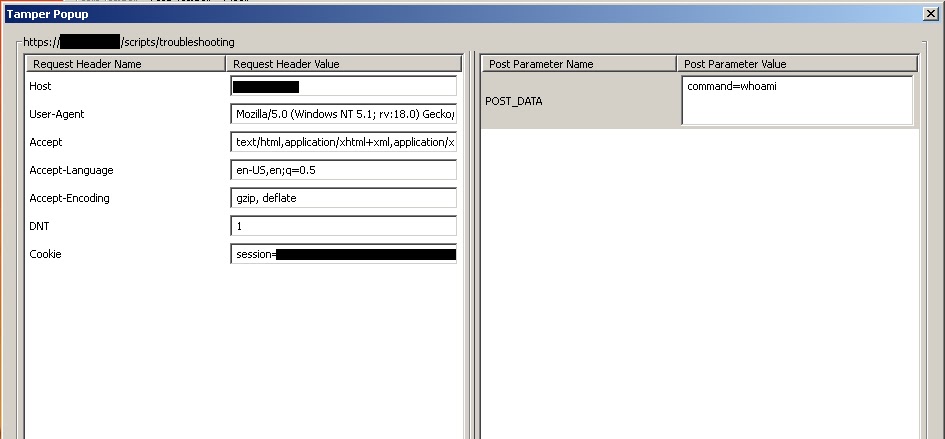
So I turned on Tamper Data plugin and set to work to figure it out.
I put in 127.0.0.1 in the host field hit submit and this is what I saw:
There in the post data I see the data I entered into the fields and the command.
As luck would have it they rely completely on the webpage to filter all input. So while I may not be able to type what I want into the field I can tamper with what actually gets sent to the system with a web proxy and put my commands in there.
After a few trial and error attempts at modifying the field data sent to the ping command I realize something.
Whoa, wait a minute, it has an option to choose the command, lets see if this is limited to the options on the page.
So I get rid of everything and just put in command=whoami
This is what pops up on the webpage when I hit submit from Tamper Data:
Now this is looking promising. I'm running as the apache user but I can execute commands outside of the available set in the drop down list.
Lets try a directory listing:
You have to encode any space characters but it seems pretty lenient on any other special characters accepting either the character outright or the hex representation.
So the theory is sound, I've found a way to issue commands directly to the system, albeit with a limited user.
Next step is to find a directory we can write to and try to upload something to get us a shell.
* While it is possible to SSH into the machine, you're not able to SSH in as root, because you don't know the password. When you SSH in as the admin user you're automatically dumped into a configuration program and you're not able to interact with the OS directly.
That's all for now.
Next episode, getting shell and the path to root.
UPDATE: Part 2 of this is located here





Try this for getting root: http://milo2012.wordpress.com/2011/04/15/hacking-shoretel-converged-conferencing-bridge/
ReplyDelete